Is Blockchain Really “Unhackable”?
January 2026: DICT said that their blockchain implementation and blockchain in general is 101% safe and un-hackable.
A Clear Explanation for Filipinos:
There has been an ongoing public debate in the Philippines after a recent statement by the DICT Secretary saying that blockchain technology is secure and not hackable.
Some people agreed. Others pushed back hard.
Comments like “Tell that to the Lazarus Group” or “What about all the hacked wallets and stolen crypto?” quickly appeared online. At first glance, these reactions seem reasonable. After all, we constantly hear news about crypto thefts, drained wallets, and breached exchanges.
But this debate is mixing different things together.
To understand what is actually hackable and what is not, we need to separate blockchain into its proper layers. Once you do that, the confusion disappears.
This article explains that separation in simple terms.
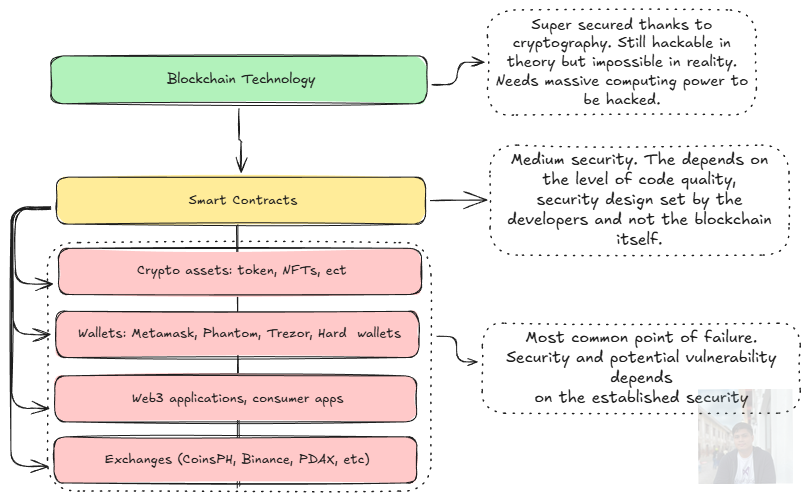
Blockchain is a Technology Stack, Not a Single Thing
When people say “blockchain,” they often imagine one big system. In reality, blockchain is a stack of technologies, each with very different security properties.
Think of it like the internet.
The internet itself has not been hacked. But websites get hacked all the time. Email accounts get compromised. Online banking fraud exists. That does not mean the internet protocol is broken.
Blockchain works the same way.
Layer 1: The Blockchain Protocol
This is the foundation.
Bitcoin, Ethereum, and other major blockchains are secured by cryptography and massive distributed computing power. Transactions are validated by thousands of independent nodes around the world.
To “hack” a major blockchain at the protocol level, an attacker would need enormous resources, usually more computing power than most countries can realistically deploy. This is why these networks have been running for years without their transaction history being altered or rewritten.
In theory, attacks are discussed in academic papers. In practice, they are not economically or technically feasible at scale.
This is what people mean when they say blockchains are secure.
Layer 2: Smart Contracts
Smart contracts are programs deployed on top of a blockchain.
They do not represent the security of the blockchain itself. They represent the quality of the code written by developers.
A smart contract can be:
Secure if it is well designed, audited, and tested
Vulnerable if it has bugs, bad logic, or unsafe assumptions
When a DeFi protocol gets drained, the blockchain was not hacked. The contract behaved exactly as it was coded to behave. The problem was that the code allowed something dangerous.
This is closer to a software bug than a cryptographic failure.
Layer 3: Wallets, Exchanges, and Applications
This is where most real-world incidents happen.
Wallets, centralized exchanges, and Web3 applications sit at the very top of the stack. They interact with users, private keys, servers, and frontends. This is also where human error exists.
Common failure points include:
Phishing attacks that trick users into signing malicious transactions
Stolen private keys
Compromised exchange infrastructure
Poor operational security
Fake websites and malicious browser extensions
When funds are stolen in these cases, the blockchain is simply recording what it was told to record. The theft happened before the transaction reached the blockchain.
Addressing the “Lazarus Group” Argument
The Lazarus Group is often cited as proof that blockchain is hackable.
This is a misunderstanding.
They do not hack the blockchain protocol. They hack:
Server infrastructure
Key management systems
Poorly secured applications
If any group could directly hack Bitcoin or Ethereum at the protocol level, the impact would not be limited to crypto users. Global finance, cybersecurity, and national infrastructure would be at risk.
That has not happened.
So Is Blockchain 100 Percent Secure?
Nothing is 100 percent secure.
Not banks. Not governments. Not the internet.
What makes blockchain different is that its core security is mathematical, not trust-based. You do not need to trust a single institution. You rely on cryptography, incentives, and decentralization.
Most failures attributed to blockchain are actually failures of software, custody, or people.
Why This Matters for Philippine Policy
As the Philippines explores frameworks like the CADENA Act, this distinction is critical.
Good regulation should focus on:
Custodial standards
Application security
Consumer protection
Operational controls
It should not treat the blockchain protocol itself as the problem when it is often the most stable and transparent part of the system.
Clear understanding leads to better laws, safer systems, and smarter adoption.
Final Thought
Blockchains are not magically immune to risk.
But they are also not the chaotic, easily hackable systems they are often portrayed to be.
Most of the time, when something goes wrong, it is not the blockchain that failed. It is the layer built on top of it.
Understanding that difference is the first step toward responsible innovation.
About the author
Koleen Paunon is a blockchain engineer and founder working at the intersection of software, security, and public policy. He builds and advises on blockchain-based systems with a focus on practical adoption and risk-awareness.Website: https://koleenbp.com
X: https://x.com/koleenbp
GitHub: https://github.com/kbpsystem777
Email: koleen.bp@outlook.com